Linux Privilege Escalation - Exploiting Weak File Permissions Part 2 (Writeable /etc/shadow /etc/passwd files)
In this post, we learn the historical significance of the /etc/passwd file, and how to exploit a writable /etc/shadow and /etc/passwd file. No password cracking required. Knowledge is power.
Greetings folks. In this post, we will be learning how to exploit weak permissions in /etc/shadow and /etc/passwd. If you haven’t read the previous post, go back and do that first. You can find that post here. If you are unfamiliar with Linux permissions, check out this post.
Exploiting writable /etc/shadow
In the previous post, we talked about exploiting a readable /etc/shadow file. But what if it’s writeable? How does that change the game?
Simply put…
A writeable /etc/shadow file means we can just replace the password hash of the root user with something we have conjured up. The process is incredibly simple.
Generate a password hash in the correct format
Replace the password hash of the root user with the one we made.
$$$Profit$$$
The default configuration of the /etc/shadow file looks like this…
In order to exploit a writeable shadow file, we need to make the file writable.
chmod u=rw,g=r,o=rw /etc/shadow
For the love of all that is Holy. Make a copy of the /etc/shadow file.
cp /etc/shadow somewheresafe
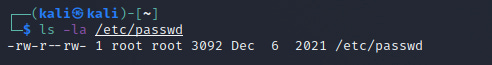
Let’s look at the amended permissions of the /etc/shadow file.
Okay so now that it is writable, we just need to create a password hash. You can do this via the mkpasswd command.
mkpasswd ashitpassword
You may need to specify the hashing algorithm. That can be done via the -m flag.
mkpasswd -m yescrypt test
or
mkpasswd -m sha-512 test
Writing to the /etc/shadow file
Now we just need to replace the password hash in the /etc/shadow file. Just use whichever editor you feel comfortable with. Vim, Gedit, Nano etc.
gedit /etc/shadow
Be careful here, ensure you paste the password hash you generated correctly. You need to paste this between the first and second “:”
Once you are confident you have pasted correctly, save the file.
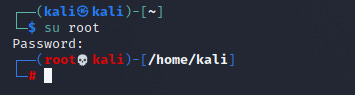
Now you should be able to log in as root, using the su command
su root
Change your password for the root user back to something secure.
Remember to also amend the permissions for /etc/shadow back to the default configuration.
chmod u=rw,g=r,o= /etc/shadow
Exploiting writable /etc/passwd
Before we exploit the /etc/passwd file. We need to learn a few key facts surrounding the historical use of /etc/passwd.
User password hashes were formerly stored in the /etc/passwd file.
For backwards compatibility, the password hash found in the second field of a user row in /etc/passwd takes precedence over the hash found in /etc/shadow.
We can simply enter a known password hash for the root user and switch to the root user using the su command if we have access to write to /etc/passwd.
An alternative is to create a new user and give them the root user ID if we can just append it to the file (/etc/passwd) . Linux supports several entries for the same user ID as long as the usernames are distinct, therefore this is possible. The user ID for root, is, of course, 0.
Before we continue, make a copy of the /etc/passwd file.
cp /etc/passwd somewheresafe
Now we have that sorted, let’s make the /etc/passwd writeable by others.
chmod u=rw,g=r,o=rw /etc/passwd
Writing to the /etc/passwd file - Method 1
In order to write a valid hash to /etc/passwd, we first need to create a valid hash. You can do this via the openssl tool.
openssl passwd rootme
Now edit the /etc/passwd file and enter the new hash we have created in the 2nd field of the root user row. Ensure that you take care here. For clarity, the 2nd row has n ‘x’ within the value.
Amend the value ‘x’ to the password hash.
Now we should be able to log in as the root user, with the “rootme” password.
Great stuff.
Writing to the /etc/passwd file - Method 2
We can use the same writeable /etc/passwd vulnerability to exploit this another way, by simply creating a new root account with the same ID as the root user “0”.
Open the /etc/passwd file again.
Copy the root account from the top of the list and paste this at the bottom, but change the username to something new, such as “dummyroot”
Save the file, now login to the user.
That’s it. Modify the permissions and file contents to the original state.
chmod u=rw,g=r,o=r /etc/passwd
That’s it for this post. In the next post, we will learn how to exploit a vulnerable sudo configuration.